The Best Startup of the Year - 2022
We are excited to announce that we have won the best startup of the year award.

Apptimate is a modular, user-friendly, and highly customizable ERP solution
which is being trusted by hundreds of businesses around the globe
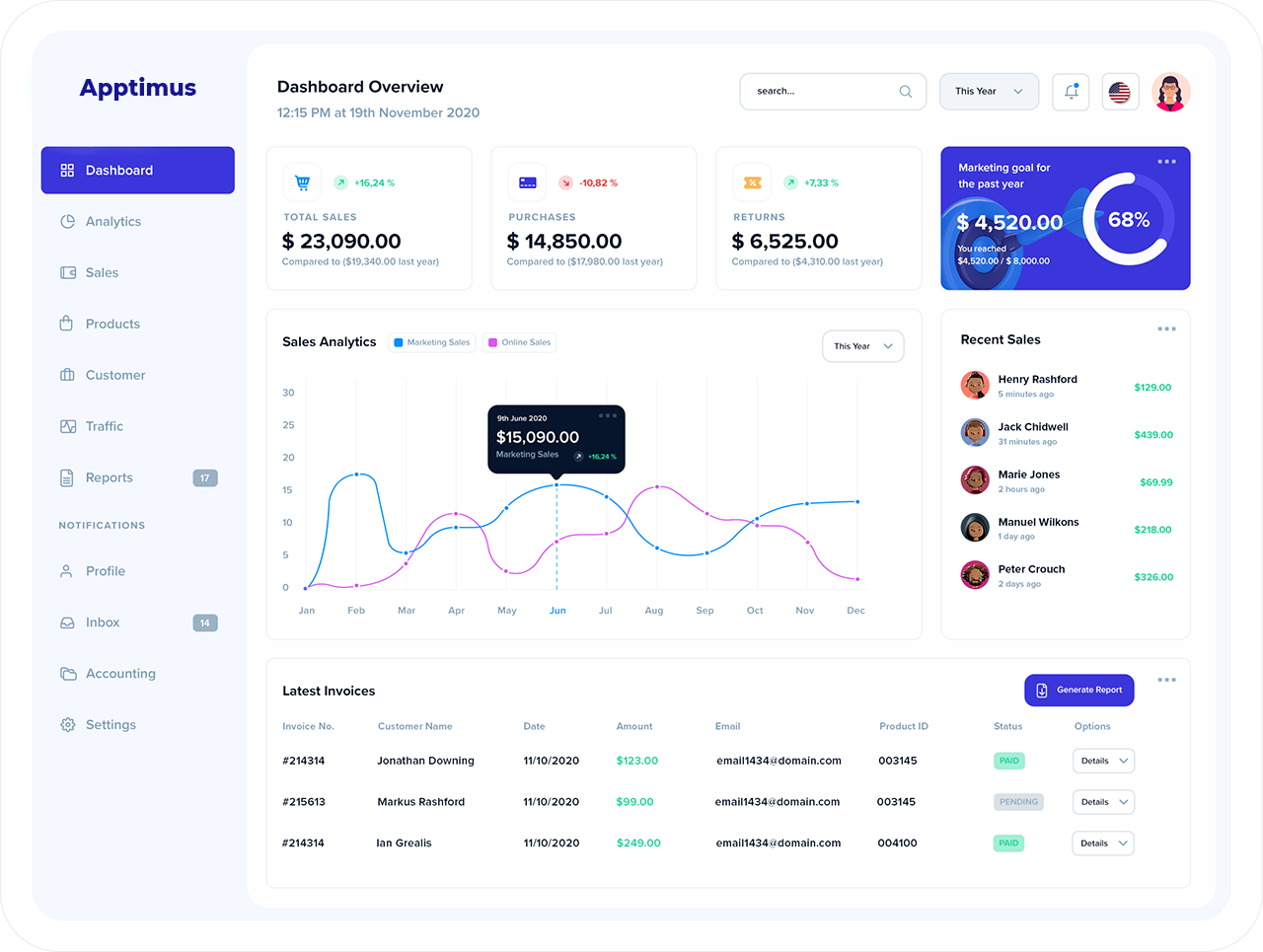
Apptimate modules are extremely customizable, integrable, and scalable
based on the business needs.

Experience the Outstanding ERP software that Sri Lanka has ever produced
Unleash Your Potential with Our Apptimate ERP. Plan, track, monitor, analyze, and optimize all the operations of your Business with a single software, instead of juggling between multiple isolated software solutions. Here is why Apptimate stands out from the rest of the ERP solutions.
All the features are UX-driven and we keep on improving them regularly
Each module can stand-alone and seamlessly work together with others
All the modules are extremely scalable and integrable with other systems
Apptimate is powered with AI-driven suggestions and alerts as needed



We are excited to announce that we have won the best startup of the year award.

Team Apptimus donated essentials for 25 underprivileged families around Myliddy and Thaiyiddy regions (Jaffna)
Let's schedule a call and talk about your Business problems/needs first. Shall we?.